Chronicles of Privacy Computing: The Cryptographic Journey to Reconstruct Trust
As artificial intelligence crosses the Turing threshold and blockchain redefines trust architectures, data itself is quietly supplanting energy as the core resource powering civilization's next evolutionary leap. Yet amidst this monumental technological transformation, we are only beginning to recognize the resurgence of an age-old dilemma: Can humanity still possess true privacy?
The greatest enemy of knowledge is not ignorance, it is the illusion of knowledge. ——Stephen HawkingThus emerges Privacy Computing. It is not merely a mutation of isolated technologies, but rather the culmination of prolonged interplay between cryptography, distributed systems, artificial intelligence, and human values. Since the theoretical frameworks of secure multi-party computation, homomorphic encryption, and other privacy-preserving technologies were established in the late 20th century, privacy computing has gradually evolved into a critical safeguard against the era of “data sovereignty crisis”—enabling collaborative computations, value sharing, and trust reconstruction while preserving raw data confidentiality.
This unfolding technological narrative represents more than just history in the making—it poses a fundamental philosophical question: "Can free will survive in an algorithmic world?" Privacy computing may well hold the first key to answering this profound dilemma.
The Germination Period (1949–1982): Foundations of Modern Cryptography
1949: Shannon and the Dawn of Information Theory
In 1949, Claude Shannon published his seminal paper "Communication Theory of Secrecy Systems," which for the first time systematically analyzed communication system security using rigorous mathematical methods. Employing information theory, he formally defined the concept of "perfect secrecy," demonstrating that only the one-time pad could satisfy such stringent security requirements. Shannon's methodology was exceptionally meticulous - he built his cryptographic models upon fundamental mathematical principles, utilizing probability theory and statistical methods. By precisely defining the concepts of entropy and information quantity, he established the theoretical foundations of modern cryptography.
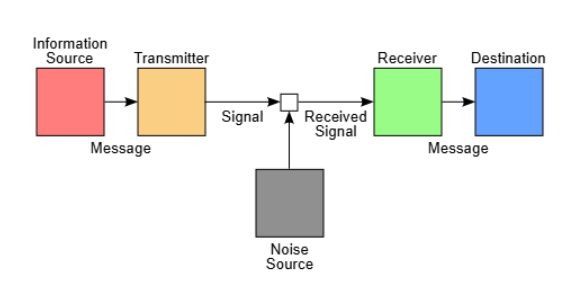
Shannon's research process was remarkably innovative. During his tenure at Bell Labs, he not only focused on theoretical work but also conducted extensive experimental verification. He had a penchant for using vivid analogies to explain complex concepts - likening information transmission to fluid flow, or entropy to uncertainty. Legend has it that he would even ride a unicycle through laboratory corridors to relax and stimulate creative thinking. The impact of this seminal paper was profound, establishing not just the theoretical foundations of modern cryptography but also shaping the research trajectory of the entire information security field for decades to come.
1976: The Diffie-Hellman Breakthrough
In 1976, Whitfield Diffie and Martin Hellman introduced the concept of public-key cryptography in their groundbreaking paper "New Directions in Cryptography," where they proposed the Diffie-Hellman key exchange protocol. Their innovative approach was based on the mathematical complexity of the discrete logarithm problem, marking the first successful demonstration of secure key exchange without requiring pre-shared secrets.
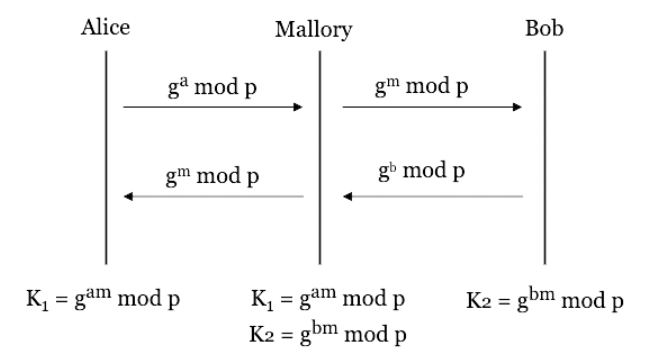
The research process was far from smooth sailing. The duo spent years in trial and error, delving deep into mathematics and number theory before finally arriving at the appropriate mathematical construct. Diffie, with his unconventional appearance and idiosyncratic demeanor, became something of a legend in academic circles - conference organizers would frequently mistake him for a rock band member. This groundbreaking work fundamentally transformed the field of cryptography, laying the foundation for digital signatures and other modern security protocols.
1977: The Birth of RSA
In 1977, MIT researchers Ron Rivest, Adi Shamir, and Leonard Adleman jointly developed the renowned RSA algorithm - the first practical asymmetric encryption system. Their groundbreaking approach leveraged the mathematical complexity of large prime factorization as its security foundation, combining sophisticated mathematical derivation with computational experimentation to successfully construct a workable asymmetric cryptographic mechanism.
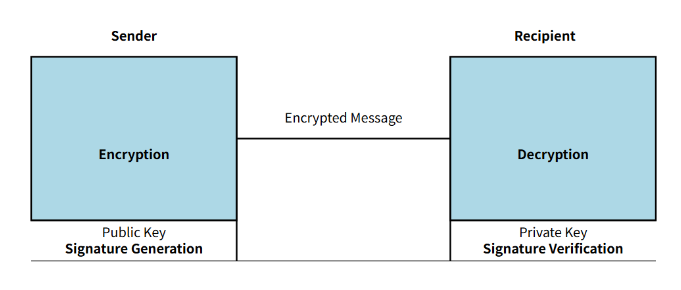
During their research, Rivest experienced a breakthrough after an all-night brainstorming session, quickly drafting the algorithm's framework, while Adleman spearheaded its implementation and verification. To commemorate this milestone, they encrypted a now-legendary message using the RSA algorithm, challenging colleagues to decrypt it. Beyond its theoretical significance, the RSA algorithm provided practical security solutions that would become fundamental to e-commerce systems, digital signatures, and other critical applications.
1978: Early Concepts of Homomorphic Encryption
In 1978, following their breakthrough with the RSA algorithm, Rivest, Shamir, and Adleman turned their attention to a groundbreaking new concept: the computational potential of encrypted data—what would later be known as homomorphic encryption. With remarkable foresight, they posed a deceptively simple question: Could an encryption system permit direct computations on ciphertext without prior decryption? Though they couldn't solve this formidable challenge at the time, their visionary inquiry ignited three decades of sustained cryptographic exploration that would ultimately revolutionize data privacy.

1979–1982: Cryptographic Renaissance
During this period, the field of cryptography witnessed numerous groundbreaking theoretical advancements. Adi Shamir introduced secret sharing schemes—an ingenious cryptographic construction employing sophisticated algebraic structures to distribute secret information among multiple parties. This approach ensures secure decentralized management of secrets, with the crucial property that reconstruction is only possible when a predefined threshold of participants collaborate.
In his research, Michael Rabin proposed the Oblivious Transfer (OT) protocol—an elegant cryptographic primitive that ingeniously resolves trust issues in information exchange. This mechanism enables one party to securely retrieve specific data while ensuring the other party remains unaware of which particular information was accessed.
In 1982, Qizhi Yao formulated the renowned "Millionaires' Problem"—a witty and vivid thought experiment that distilled complex cryptographic concepts into an intuitive scenario: how to securely determine who is wealthier between two parties without revealing their actual financial amounts. Yao's methodology employed abstract logical deduction and game-theoretic approaches, with this seminal work directly inspiring the subsequent research boom in Secure Multi-Party Computation (MPC). His foundational contribution significantly advanced cryptography's applications in privacy-preserving information sharing and secure data collaboration.
Collectively, these profound and rigorous research breakthroughs catalyzed the initial flourishing of modern cryptography, laying a robust theoretical and technical foundation for future advancements in the field.
The Exploration Era (1983–1999): Theoretical Breakthroughs and Early Privacy Tools
1985: Birth of Zero-Knowledge Proofs
In 1985, MIT researchers Shafi Goldwasser, Silvio Micali, and Charles Rackoff introduced the groundbreaking concept of Zero-Knowledge Proofs (ZKP). Building upon their work on interactive proof systems, they posed a fundamental question: How can one prove knowledge of a secret without revealing the secret itself? Through sophisticated interactive protocols and probabilistic methods, they devised a verification process where the verifier becomes convinced of the prover's knowledge while remaining completely unable to deduce any specific information about the secret.
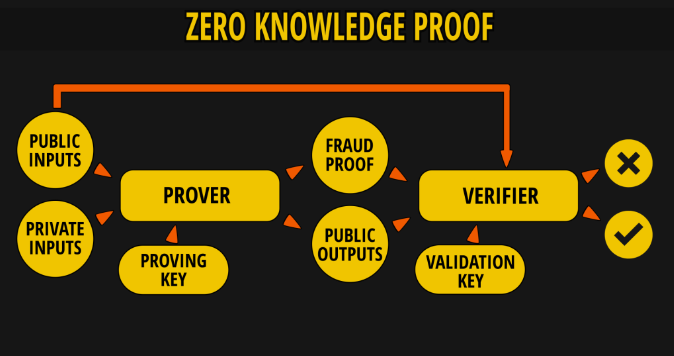
An interesting anecdote: The initial inspiration for this research came from a simple card game. During an academic conference, the team demonstrated ZKP concepts through an interactive game, leaving the audience both amazed and perplexed. The introduction of ZKP not only provided a crucial theoretical tool for modern cryptography, but also established essential technical foundations for privacy computing. Its profound influence extends to subsequent developments in anonymous authentication, privacy protection, blockchain technology, and beyond.
1986–1987: Advancements in Secure Multi-Party Computation
In 1986, Professor Qizhi Yao introduced the groundbreaking Garbled Circuits technique, ingeniously realizing secure two-party computation protocols. His approach transformed computational functions into complex circuits that were then cryptographically garbled before being executed by the counterparty - ensuring correct output generation while preventing any visibility into the original input data. Yao's pioneering methodology bridged cryptography with computational complexity theory, marking a seminal breakthrough in computer science.
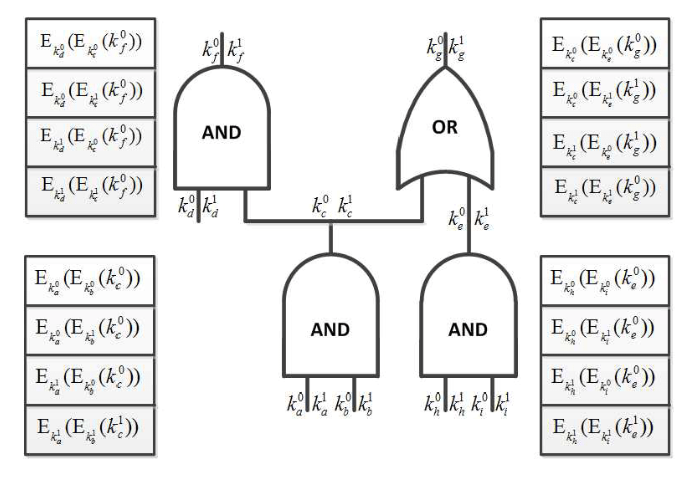
An interesting fact: Yao's unique interdisciplinary background often led him to approach problems from unexpected angles, earning him the playful academic nickname of the "Dark Wizard of Cryptography." Shortly thereafter, in 1987, Oded Goldreich, Silvio Micali, and Avi Wigderson proposed the renowned GMW Protocol, extending secure multi-party computation (MPC) to multi-party scenarios. This allowed multiple participants to jointly execute computations without revealing their private input data. These breakthroughs substantially advanced both the theory and practical implementation of MPC, transforming privacy-preserving computation from a theoretical concept into a tangible possibility.
1996: Early Conceptualization of Federated Learning
In 1996, David W. Cheung proposed an association rule mining algorithm for distributed systems. Although the specific term "federated learning" had not yet been formally introduced at that time, the core concept of his research remarkably aligned with what would later become the fundamental principle of federated learning. His distributed data mining approach eliminated the need for centralizing all data, instead enabling multiple independent data owners to process their data locally and exchange only the mining results.
Cheung's research journey carries particular intrigue: initially aimed at solving data mining challenges for large enterprises, his work inadvertently established a theoretical prototype for what would later become federated learning. At the time, his findings attracted limited attention. It wasn’t until two decades later—as privacy concerns escalated and companies like Google began adopting federated learning at scale—that the prescient value of this work became fully apparent.
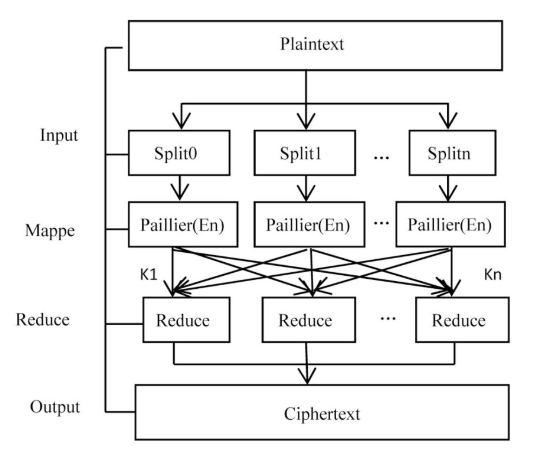
1999: Practical Implementation of Additive Homomorphic Encryption
In 1999, Pascal Paillier proposed a novel additive homomorphic public-key cryptosystem that enabled direct addition operations on ciphertexts without decryption. This breakthrough addressed long-standing practical implementation challenges in homomorphic encryption. By employing group-theoretic mathematical constructs, Paillier achieved secure additive homomorphic properties, allowing efficient processing of data while remaining encrypted. This work significantly advanced real-world applications of encrypted data computation.
The Paillier cryptosystem has been widely adopted in practical applications such as electronic voting and privacy-preserving data analysis. According to reports, Paillier's initial inspiration for designing this scheme came from addressing privacy concerns in anonymous e-voting systems. This needs-driven research approach not only carried theoretical significance but also significantly accelerated the industrial adoption of homomorphic encryption technology.
During this period, cryptographic theory flourished remarkably, with continuous emergence of innovative techniques and methodologies. These advancements laid a solid foundation for the vigorous development of privacy computing while providing a rich toolkit for future technological applications.
The Growth Period (2000–2018): Formalization of Privacy Computing Frameworks
2006: The Advent of Differential Privacy
In 2006, Cynthia Dwork from Microsoft Research introduced differential privacy, a groundbreaking theory that provided rigorous mathematical guarantees for data privacy protection in the big data era. Dwork's innovative approach artfully incorporated random noise into query results, ensuring that the inclusion or exclusion of any single data record would have negligible impact on the overall output—thereby effectively safeguarding individual privacy.
An intriguing anecdote: During early efforts to promote differential privacy, Dwork famously used a telephone directory as a case study to vividly demonstrate real-world privacy risks. She revealed that while anonymized datasets might appear secure, auxiliary information could still be used to reconstruct sensitive details. Her work established new standards for data privacy protection and has been widely adopted in healthcare data analysis, demographic studies, and social science research—profoundly shaping the trajectory of subsequent privacy computing technologies.
2009: Breakthroughs in Fully Homomorphic Encryption and Trusted Execution Environments (TEE)
2009 marked a pivotal year for cryptographic advancements. A seminal development emerged when the Open Mobile Terminal Platform (OMTP) first proposed the precursor to Trusted Execution Environments (TEE), aiming to establish hardware-level isolated secure environments for protecting sensitive data on mobile devices.
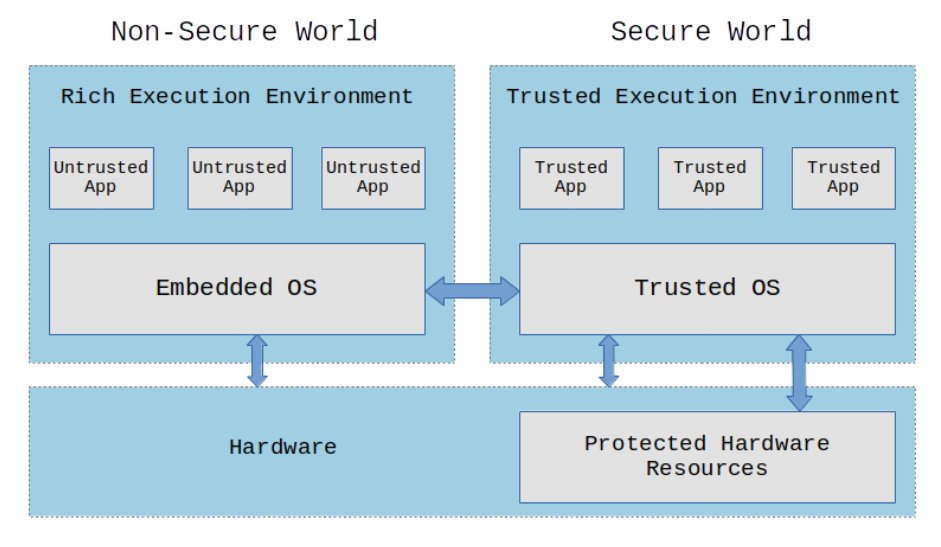
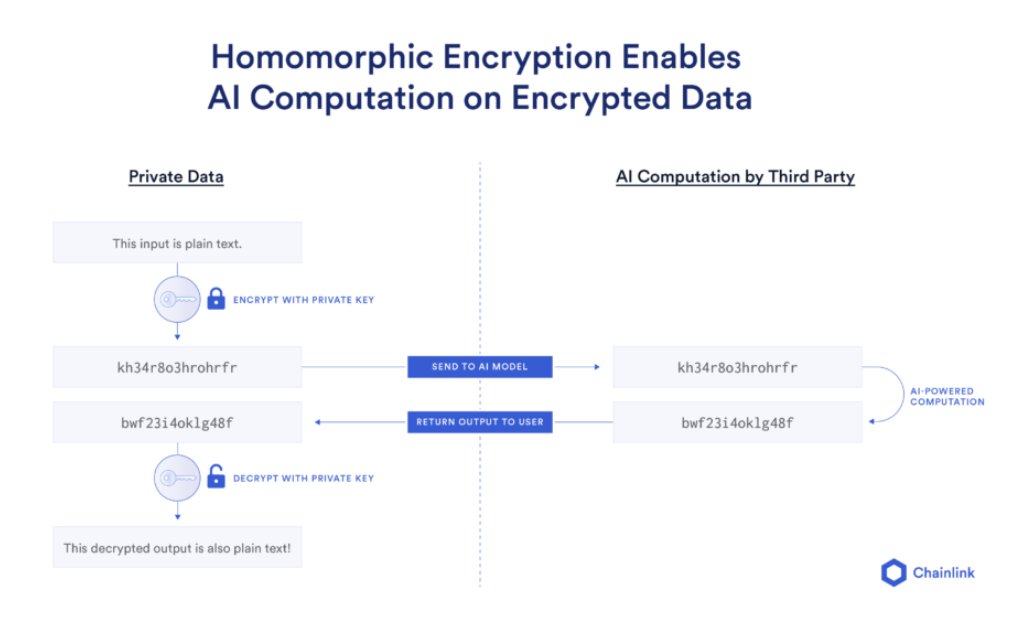
In the same year, IBM's Craig Gentry unveiled the first fully homomorphic encryption (FHE) scheme—a revolutionary breakthrough that enabled arbitrary computations on encrypted data without requiring decryption. Gentry's research journey reads like an academic legend: after years of hitting theoretical walls, a sudden epiphany during a casual walk reportedly helped him solve this decades-old cryptographic puzzle that had baffled researchers.His breakthrough inaugurated a new era of ciphertext computation, enabling secure and efficient applications of encrypted data in cloud computing, financial data analytics, and other critical scenarios.
2013: Pioneering Work in Medical Federated Learning
In 2013, Professor Shuang Wang's team pioneered the EXPLORER medical federated learning system, marking the first practical implementation of secure model training on distributed healthcare data. By innovatively integrating distributed machine learning with privacy-preserving techniques, the team developed a cross-institutional collaborative training methodology that operates without requiring raw data sharing.
Reportedly, this research was initially motivated by the practical challenges of medical data sharing. Through multiple technical iterations and cross-disciplinary collaborations, the team ultimately established a secure framework for sharing medical data without compromising patient privacy. The EXPLORER system rapidly became an international benchmark for healthcare data protection, pioneering new global practices for secure medical data collaboration.
2015–2016: Milestones in Privacy Computing Industrialization
The period from 2015 to 2016 marked pivotal milestones in the industrialization of privacy computing. Intel Corporation launched SGX (Software Guard Extensions), the first commercial implementation of Trusted Execution Environment (TEE) technology, enabling hardware-level isolated execution of applications to safeguard sensitive data and processes. This breakthrough brought privacy protection into practical applications, including secure cloud computing and financial transactions.
At the same time, Google's AI team proposed the Federated Learning framework in 2016, directly integrating the concept of privacy computing into mobile terminal applications. Federated Learning enables data to be trained locally on devices, then aggregates the model parameters centrally without requiring direct uploading of sensitive data. This approach not only improves data security but also significantly enhances user privacy protection capabilities.
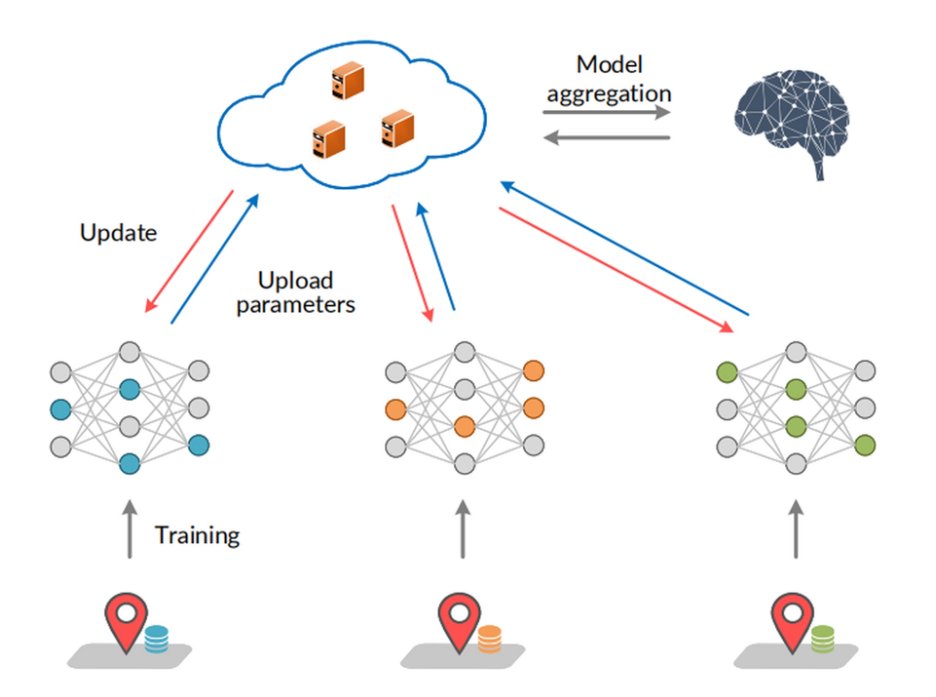
Interestingly, Google's federated learning project was initially code-named the "Honeybee Project" internally—a metaphor suggesting how multiple endpoints, like worker bees, could collectively contribute to and ultimately converge into a unified intelligent model. This vivid analogy also reflects how privacy-preserving computing technologies have evolved from abstract theoretical concepts to practical, real-world applications.
The Application Era (2019–2024): Privacy Computing Goes Mainstream
2019: Federated Transfer Learning & Birth of FATE Framework
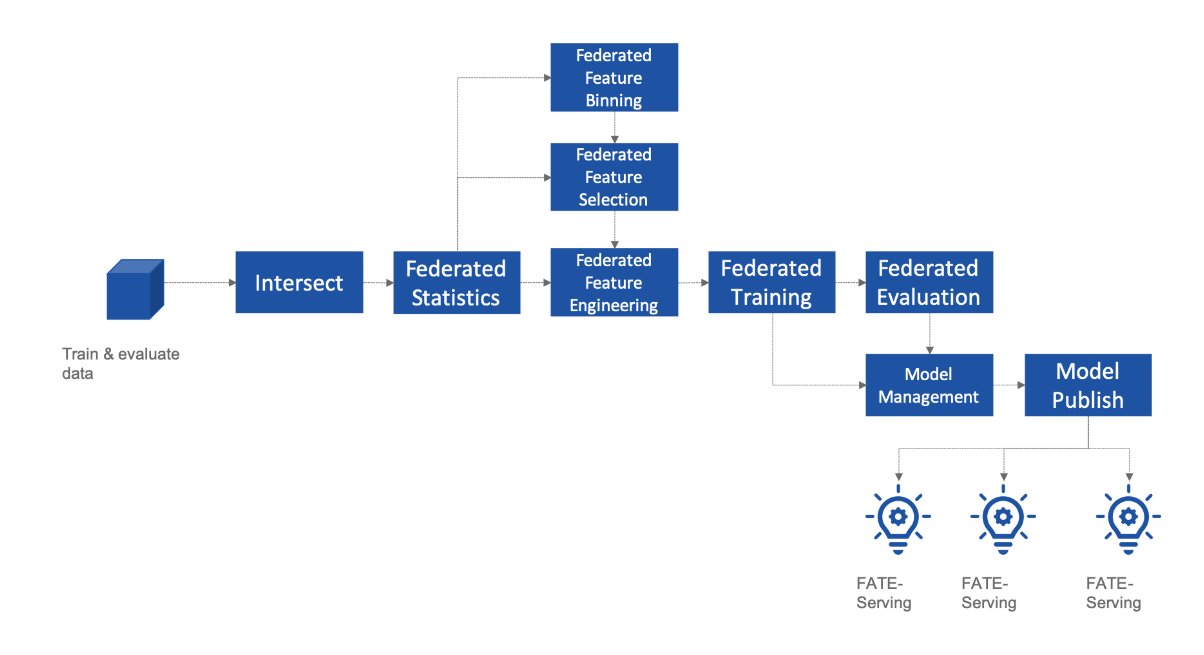
In 2019, Professor Qiang Yang and his team at the Hong Kong University of Science and Technology officially introduced the theory of Federated Transfer Learning and the open-source framework FATE (Federated AI Technology Enabler), significantly advancing the industrialization and engineering implementation of federated learning technology.Professor Yang's team pioneered an innovative approach that combines federated learning with transfer learning, enabling models and knowledge to be shared across different domains and scenarios without exchanging raw data—effectively addressing the longstanding challenge of data silos.
An interesting anecdote: During FATE's official open-source launch event, industry interest was so overwhelming that attendance far exceeded expectations—forcing organizers to urgently secure a larger venue. This episode vividly reflects the tremendous enthusiasm and anticipation surrounding federated learning's real-world implementation.
The introduction of the FATE system not only accelerated the real-world adoption of federated learning technology, but also established a foundational technical framework for subsequent data collaborations. It was rapidly deployed in practical applications such as financial risk management, medical diagnosis, and smart government services, providing tangible solutions that reconcile data sharing with privacy protection.
Privacy Computing as Data Infrastructure
With the advent of the data era, the data factor market has experienced rapid development, making data security and privacy protection core concerns across industries. Meanwhile, increasingly stringent data compliance requirements worldwide have accelerated the deep integration of privacy-preserving computing technologies with critical sectors such as finance, healthcare, and government services.
In the financial sector, privacy-enhancing technologies like Fully Homomorphic Encryption (FHE), Secure Multi-Party Computation (MPC), and Zero-Knowledge Proofs (ZKP) are widely deployed for risk control and anti-fraud applications, ensuring secure and compliant data utilization. Within healthcare, Differential Privacy (DP) and Federated Learning (FL) technologies effectively safeguard patient confidentiality while enabling cross-institutional medical research collaborations.
In the government sector, Trusted Execution Environment (TEE) technology has been actively adopted to establish secure and efficient public data processing platforms, ensuring both sensitive information security and maintenance of public trust. The synergistic application of these technologies has significantly accelerated the unleashing of data value while enhancing the efficiency and security of data sharing.
Technological Convergence & Industrial Integration
At the current stage, multiple core cryptographic technologies—including Zero-Knowledge Proofs (ZKP), Secure Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), Trusted Execution Environment (TEE), Differential Privacy (DP), and Federated Learning (FL)—are progressively converging toward a co-evolutionary development path. This technological convergence not only diversifies privacy preservation methodologies but also elevates the overall practicality and reliability of privacy-preserving computing systems.
Privacy computing has transcended theoretical research to become a widely adopted infrastructure that enables secure data circulation and value sharing, fostering a new ecosystem of "privacy-preserving technologies + industries." Moving forward, these technologies will become further embedded in digital transformation initiatives across sectors, serving as a critical engine for industrial innovation, economic growth, and societal advancement.
These substantial theoretical explorations and successful technological implementations mark a new era where cryptography and privacy computing have achieved practical maturity, while also laying a solid foundation for the development of high-performance cryptographic applications.
Cryptography for All (2025–Present): The ZEROBASE Era
2025: Rise of ZEROBASE & Inclusive Privacy Computing
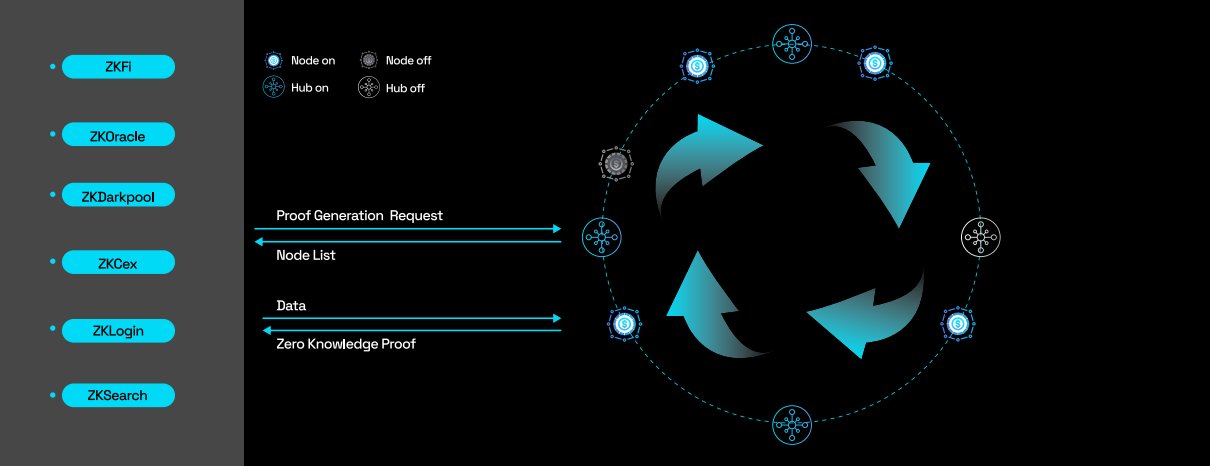
The year 2025 marked the beginning of an entirely new phase for privacy computing—the ZEROBASE era. The ZEROBASE project uniquely brought privacy computing into the daily lives of ordinary users. Its vision is to build a global Zero-Knowledge (ZK) trust infrastructure that supports the implementation of privacy computing applications across various fields including finance, government services, and healthcare.
ZEROBASE adopts a decentralized and user-friendly architecture to lower the technical barriers for users to participate in privacy computing. It has redesigned the trusted setup process for Zero-Knowledge Proof (ZKP) systems, achieving for the first time a trusted setup (Trusted Setup) through a browser combined with an image entropy source.

In early 2025, ZEROBASE initiated a Guinness World Records challenge, successfully attracting over 564,000 global users to participate in the prelaunch activities through OKX Wallet during the warm-up phase.
ZEROBASE: Technological Innovation Meets Social Consensus
ZEROBASE presents complex cryptographic technologies through user-friendly interfaces, enabling previously sophisticated trusted setups to be completed with simple image uploads and browser operations. This design philosophy not only lowers the participation barrier but also transforms ZK technology into a social movement, significantly enhancing public awareness and acceptance of privacy-preserving computing.
On the technical front, ZEROBASE has developed highly optimized ZKP circuits capable of generating over 1,000 proofs per second, propelling it to a leading position in the ZK proof market. The platform has also launched several groundbreaking applications:
-
zkLogin: Frictionless Web3 authentication
-
zkCEX: Hybrid exchange model combining on-chain order matching with off-chain settlement
-
zkStaking: Staking system that validates arbitrage risks while optimizing yield generation
Significance of ZEROBASE's Guinness World Record Challenge
ZEROBASE's Guinness World Records challenge represents not merely a technological breakthrough, but a fundamental shift in social narrative. Unlike traditional trusted setup ceremonies, this initiative transforms privacy computing from a mysterious "black box" into an open, transparent, and participatory social phenomenon. Through mass participation mechanisms and publicly verifiable processes, ZEROBASE has effectively addressed the long-standing trust and consensus challenges in ZK technology.

This Guinness World Records achievement demonstrates that:
-
Privacy-preserving technologies can achieve mass public engagement
-
Technological accessibility and social consensus are equally crucial as technical innovation
The implications are clear: the future of privacy computing lies not in complex technical stacks, but in creating barrier-free participation pathways for everyday users.
Playground Entrance: https://zerobase.pro/playground/index.html
Future Vision: Building Global Privacy Computing Infrastructure
As privacy-preserving computing gradually moves beyond the laboratory, it is quietly reshaping the fundamental order of human collaboration. In the future, we may no longer need to worry about every instance of data sharing, as privacy protection will become a system-default "fundamental right": a farmer could use privacy algorithms to predict climate change; a community could manage public affairs through DAOs without intermediaries; a patient in a remote area could securely share medical records using trusted AI to obtain globally optimal solutions.
Looking further ahead, we may witness privacy-preserving computing serving as civilization's last line of defense in the quantum era, becoming the "secure anchor star" for the trusted operation of digital society. Looking back today, this transformation may have only just begun. But just as the internet evolved from protocols to global ubiquity, privacy-preserving computing will ultimately reach every ordinary individual. What truly merits remembrance is not any single technological breakthrough, but rather how we collectively choose to advance toward a digital civilization that is more free, more secure, and more trustworthy.
Reference
[1] Shamir A. How to share a secret. Commun ACM. 1979 Nov;22(11):612–3.
[2] Diffie W, Hellman M. New directions in cryptography. IEEE Trans Inf Theory. 1976 Nov;22(6):644–54.
[3] Calderbank. The rsa cryptosystem: history, algorithm, primes. Chicago: math uchicago edu [Internet].
[4] Yao AC. Protocols for secure computations. In: 23rd Annual Symposium on Foundations of Computer Science (sfcs 1982). 1982. p. 160–4.
[5] Shannon CE. Communication theory of secrecy systems. The Bell System Technical Journal. 1949 Oct;28(4):656–715.
[6] Blakley. Safeguarding cryptographic keys. In: Managing Requirements Knowledge, International Workshop on. 1979. p. 313.
[7] Rabin MO. How To Exchange Secrets with Oblivious Transfer. Cryptology ePrint Archive [Internet]. 2005.
[8] Rivest RL, Adleman L, Dertouzos ML. On data banks and privacy homomorphisms. Foundations of secure [Internet]. 1978.
[9] Goldwasser S, Micali S, Rackoff C. The knowledge complexity of interactive proof-systems [Internet]. Proceedings of the seventeenth annual ACM symposium on Theory of computing - STOC ’85. 1985.
[10] Yao ACC. How to generate and exchange secrets. In: 27th Annual Symposium on Foundations of Computer Science (sfcs 1986). 1986. p. 162–7.
[11] Goldreich O, Micali S, Wigderson A. How to Play ANY Mental Game. In: Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing. New York, NY, USA: ACM; 1987. p. 218–29. (STOC ’87).
[12] Diffie W, Hellman M. New directions in cryptography. IEEE Trans Inf Theory. 1976 Nov;22(6):644–54.
[13] Paillier P. Public-Key Cryptosystem Based on Discrete Logarithm Residues. EUROCRYPT 1999 [Internet].
[14] Dwork C. Differential Privacy. In: Automata, Languages and Programming. Springer Berlin Heidelberg; 2006. p. 1–12.
[15] Hardware Working Group. ADVANCED TRUSTED ENVIRONMENT: OMTP TR1 [Internet]. OMTP Limited; 2009.
[16] Gentry C. A fully homomorphic encryption scheme [Internet]. 2009. Available.
[17] Wang S, Jiang X, Wu Y, Cui L, Cheng S, Ohno-Machado L. EXpectation Propagation LOgistic REgRession (EXPLORER): distributed privacy-preserving online model learning. J Biomed Inform. 2013 Jun;46(3):480–96.
[18] Gao D, Liu Y, Huang A, Ju C, Yu H, Yang Q. Privacy-preserving Heterogeneous Federated Transfer Learning. In: 2019 IEEE International Conference on Big Data (Big Data). 2019. p. 2552–9.
[19] Kone ny J, Brendan McMahan H, Yu FX, Richtárik P, Suresh AT, Bacon D. Federated Learning: Strategies for Improving Communication Efficiency [Internet]. arXiv [cs.LG]. 2016.
[20] Intel. Intel Architecture Instruction Set Extensions Programming Reference [Internet]. Intel; 2015.